Role and User Management
In this chapter:
Predefined Roles
FindFace Multi provides the following predefined roles:
Administrator is granted full access to the FindFace Multi functionality, integrative and administrative tools.
Important
Whatever the role, the first administrator (Super Administrator) cannot be deprived of its rights.
Operator is granted full access to the FindFace Multi functionality.
User is granted rights to modify their profile and work with events and episodes. The other functions are available read-only.
You can change the predefined roles privileges, as well as create various custom roles.
Create Custom Role in UI
To create a custom role in the web interface, do the following:
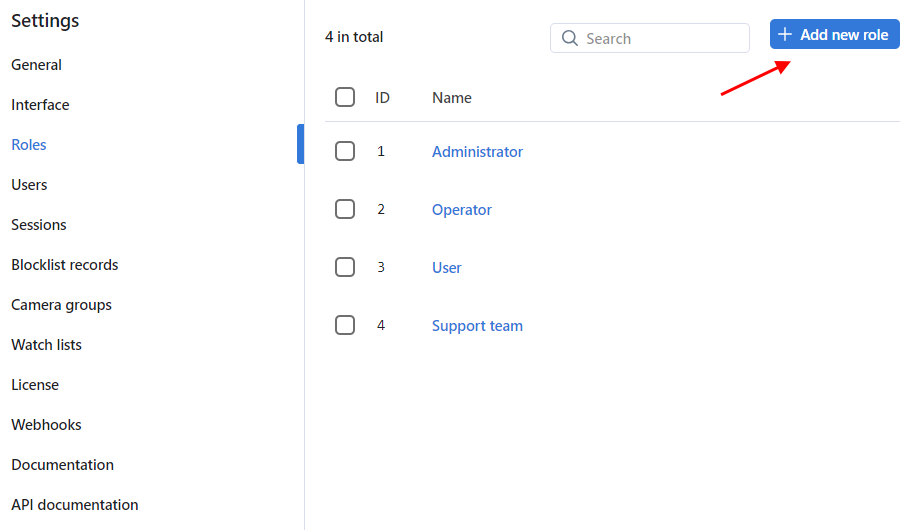
Navigate Settings -> Roles.
Click + Add new role.
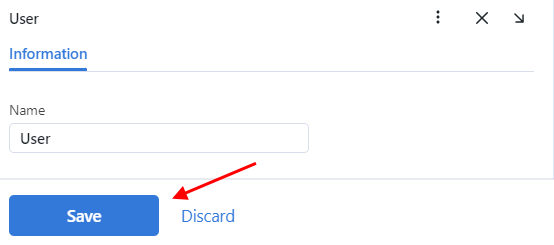
On the Information tab, specify the role name. Save the role.
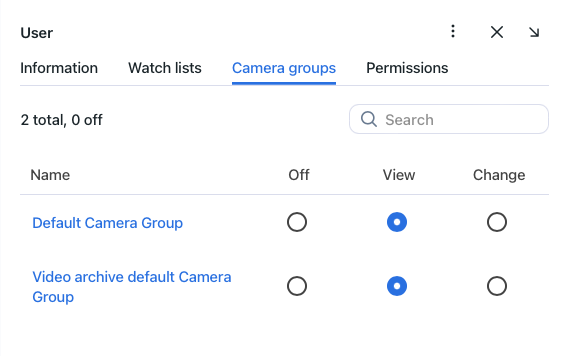
After saving the role, you will see the following tabs appear next to the Information tab:
Watch Lists: role privileges for specific watch lists
Camera Groups: role privileges for specific camera groups
Permissions: role privileges for entire system functions and entities
Set role privileges, subject to your needs. Note that there is a distinction between role privileges for a specific watch list/camera group and a system entity with the name
watchlist/cameragroup. For example, if you setOfffor a certain camera group on the Camera Groups tab, users with this role won’t be able to work with this very group of cameras. Unchecking all checkboxes for thecameragroupentity on the Permissions tab will prevent users from viewing and working with all camera groups.The full list of the FindFace Multi entities which are used in the current version is as follows:
all_own_sessions: all sessions of the current user on different devicesNote
If relevant permissions for this entity are set, users will be able to view (
view) and close (delete) all their sessions on different devices. Otherwise, users will be only allowed to view and close their session on the current device. Working with sessions takes place on the Sessions tab (Settings).bodycluster: cluster of bodiesbodyevent: body recognition eventbodyobject: full-length photo in a recordcamera: cameracameragroup: camera groupcarcard: vehicle recordcarcluster: cluster of vehiclescarepisode: vehicle-related episodecarevent: vehicle recognition eventcarobject: vehicle photo in a recordcounter: countersdeviceblacklistrecord: blocklistfacecluster: cluster of facesfaceevent: face recognition eventfaceobject: face photo in a recordhumancard: record of an individualhumanepisode: person-related episodereport: reportupload: item (photo) in batch photo uploaduploadlist: list of photos in batch uploaduser: uservideoarchive: object identification in video fileswatchlist: watch listwebhook: webhook
You can also enable and disable rights for the following functionality:
batchupload_cards: bulk record uploadchange_runtimesetting: changing the FindFace Multi general settingsview_auditlog: viewing and working with the audit logs.configure_ntls: configuration of thefindface-ntlslicense serverview_runtimesetting: viewing the FindFace Multi general settings
Save the changes.
Primary and Additional User Privileges
You assign privileges to a user by using roles:
Primary role: main user role, mandatory for assignment. You can assign only one primary role to a user.
An additional user role, optional for assignment. You can assign several roles to one user. The rights associated with the additional roles will be added to the primary privileges.
All users belonging to a particular primary role automatically get access to camera groups (and video archives within the group) and watch lists (and records in the watch list) created by a user with the same primary role, subject to the privileges defined by their additional role(s).
See also
Create User Account Manually
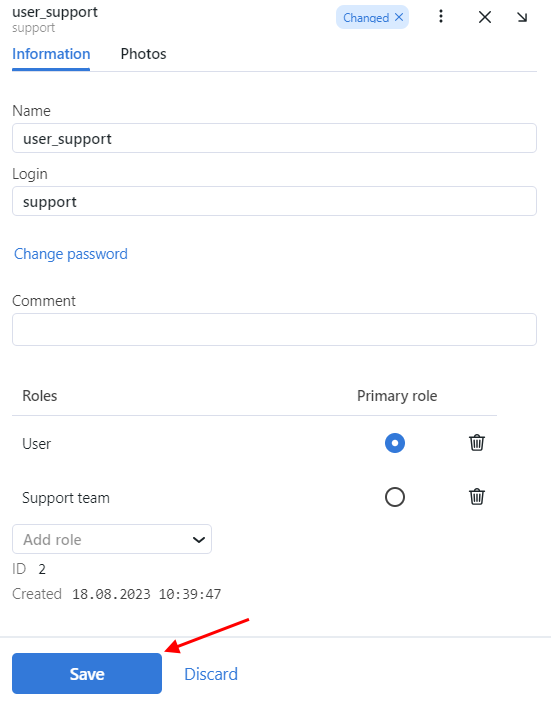
To create a user account manually, do the following:
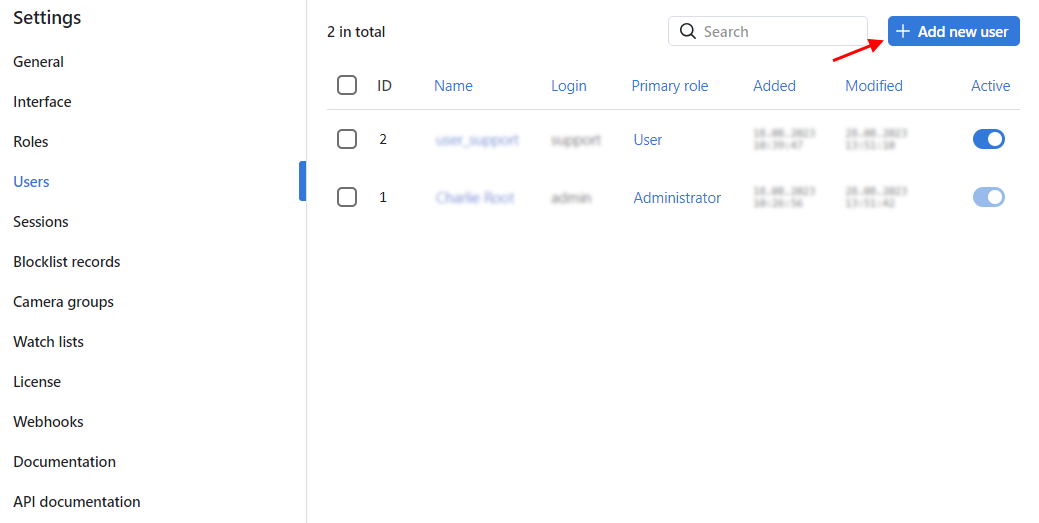
Navigate Settings -> Users.
Click + Add new user.
On the Information tab, specify user data such as name, login, and password. If necessary, add a comment.
Note
When setting a password, mind password requirements:
at least 8 characters long
not only numerals
not within the list of 20000 commonly used passwords
not similar to other user attributes
only Latin letters, numerals, and special characters are allowed
From the Roles drop-down menu, select one or several user roles. Set one of them as the Primary role.
On the Photos tab, attach the user’s photo.
Save the user account.
Work with Roles and Users via Console
In case predefined roles have been removed from the system, use the following command to create them:
sudo docker exec -it findface-multi-findface-multi-identity-provider-1 /opt/findface-security/bin/python3 /tigre_prototype/manage.py create_groups
To create a user with Super Administrator rights (superuser), execute the following command, mind that password is a required argument:
sudo docker exec -it findface-multi-findface-multi-identity-provider-1 /opt/findface-security/bin/python3 /tigre_prototype/manage.py create_default_user --password <password>
Integrate with Active Directory for Auto User Creation
If there are many users in FindFace Multi, it can be inconvenient to create their accounts one by one. One of the ways to facilitate the user creation is to harness the FindFace Multi integration with Active Directory. To do so, follow the step-by-step instructions below, minding the sequence.
Generate Keytab File
Log-in into the Active Directory server and do the following:
Create a new user account in the Active Directory domain to use as a service account.
Do the following:
Open Active Directory. Click Start, point to Administrative Tools, and then click Active Directory Users and Computers.
Click the domain name and then expand the contents. Right-click Users, point to New, and then click User. You will see a user creation form.
Fill-in the fields in the form at your discretion. On the second tab, check the Password never expires checkbox.
Click Next. Review the information that you provided, and if everything is correct, click Finish.
Right-click the just created user account, and then navigate Properties -> Member Of -> Add.
In the Select Groups dialog box, add the Domain Administrators and Domain Users groups to the list, and then click OK.
Click OK to finish.
Register a Service Principal Name (SPN) for the service account that you created. To do so, open PowerShell as administrator and execute the following command, specifying your actual
SERVICE USER NAMEand domain. In the example below, the domain name istestntl.local.setspn -A HTTP/<SERVICE USER NAME>.testntl.local@TESTNTL.LOCAL <SERVICE USER NAME>
In the same PowerShell window, generate a Keytab file by executing the command below with your actual
SERVICE USER NAME, domain, and desirableKEYTAB FILE NAME.ktpass.exe -princ HTTP/<SERVICE USER NAME>.testntl.local@TESTNTL.LOCAL -mapuser <SERVICE USER NAME> -crypto ALL -ptype KRB5_NT_PRINCIPAL -pass * -out c:\<KEYTAB FILE NAME>.keytab
To check the result, navigate to the root directory of the
Cdrive. You will see a keytab file with the relevant name.Move the keytab file that you created to the FindFace Multi server.
Configure Volumes for Kerberos and Keytab File
To successfully establish a link between FindFace Multi and Active Directory, you need to enable the Kerberos support in the findface-multi-findface-multi-ui-1 container on the FindFace Multi principal server. Do the following:
Mount the
/opt/findface-multi/configs/kerberos/krb5.conffile and the/opt/findface-multi/configs/keytabdirectory into thefindface-multi-findface-multi-ui-1container. To do so, open the/opt/findface-multi/docker-compose.yamlconfiguration file and list them in the volumes of thefindface-multi-uisection.sudo vi /opt/findface-multi/docker-compose.yaml findface-multi-ui: ... volumes: ['./configs/findface-multi-ui/nginx-site.conf:/etc/nginx/conf.d/default.conf:ro', './data/findface-multi-legacy/uploads:/var/lib/findface-security/uploads', './configs/kerberos/krb5.conf:/etc/krb5.conf:ro', './data/findface-multi-ui/keytab/:/keytab/']
Create directories for the mounted volumes:
/opt/findface-multi/configs/kerberos/and/opt/findface-multi/data/findface-multi-ui/keytab/. Copy the Kerberos configuration file from thefindface-multi-findface-multi-ui-1container to the/opt/findface-multi/configs/kerberos/directory.sudo mkdir -p /opt/findface-multi/data/findface-multi-ui/keytab/ sudo mkdir /opt/findface-multi/configs/kerberos/ sudo docker cp findface-multi-findface-multi-ui-1:/etc/krb5.conf /opt/findface-multi/configs/kerberos/
Open the
/opt/findface-multi/configs/kerberos/krb5.confconfiguration file. Specify the Active Directory realm in thelibdefaultssection. It must be equal to the Active Directory domain name, but spelled in upper case (TESTNTL.LOCALin the example below). Specify the Active Directory domain in therealmssection as well by analogy with the example below.sudo vi /opt/findface-multi/configs/kerberos/krb5.conf [libdefaults] default_realm = TESTNTL.LOCAL ... [realms] TESTNTL.LOCAL = { kdc = testntl.local default_domain = testntl.local }
Copy the keytab file to the
/opt/findface-multi/data/findface-multi-ui/keytab/directory.Append the following string to the
/etc/hostsfile:<Active Directory server IP address> <Active Directory domain name>.vi /etc/hosts ... 192.168.0.5 testntl.local
Configure NGINX on FindFace Multi Server to Support Active Directory
Open the
/opt/findface-multi/configs/findface-multi-ui/nginx-site.confconfiguration file. Find thelocation /users/me/adsection and uncomment it. Fill in the section by analogy with the example below, placing your actual variables in the strings with comments (#).The variables to specify are the following:
auth_gss_realm: realm name in Kerberosauth_gss_keytab: location of the keytab file.auth_gss_service_name: full service user name in Active Directory, including the name of the domain it belongs to
sudo vi /opt/findface-multi/configs/findface-multi-ui/nginx-site.conf location /users/me/ad { proxy_pass http://127.0.0.1/auth/ad_login/; # e.g http://127.0.0.1/auth/ad_login/; proxy_method POST; proxy_set_header X-Real-IP $remote_addr; proxy_set_header Host $http_host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Authorization $http_authorization; proxy_pass_header Authorization; proxy_no_cache 1; proxy_cache_bypass 1; auth_gss on; auth_gss_realm TESTNTL.LOCAL; # e.g. TESTNTL.LOCAL; auth_gss_keytab /keytab/user.keytab; # e.g. /var/lib/web.keytab auth_gss_service_name HTTP/user.testntl.local; # e.g. HTTP/web.testntl.local; auth_gss_allow_basic_fallback on; }
Finalize FindFace Multi Configuration
To finalize the FindFace Multi integration with Active Directory, perform the following configuration steps on the FindFace Multi side:
Open the
/opt/findface-multi/configs/findface-multi-legacy/findface-multi-legacy.pyconfiguration file.sudo vi /opt/findface-multi/configs/findface-multi-legacy/findface-multi-legacy.py
In the
SERVICESsection, set"active_directory": True.SERVICES = { ... "active_directory": True, ... } }
Fill in the
ACTIVE_DIRECTORY_CONFIGsection as follows:AUTH_LDAP_SERVER_URI:ldap: <Active Directory server IP address>AUTH_LDAP_BIND_DN: the name of the service user that you created in Active DirectoryAUTH_LDAP_BIND_PASSWORD: the service user passwordSEARCH_GROUPS: Active Directory organization units which FindFace Multi will search for user accounts
# Specify server credentials ACTIVE_DIRECTORY_CONFIG = { 'AUTH_LDAP_SERVER_URI': 'ldap://192.168.0.5', # Domain Administrator user 'AUTH_LDAP_BIND_DN': '<SERVICE USER NAME IN ACTIVE DIRECTORY>', # Domain Administrator user password 'AUTH_LDAP_BIND_PASSWORD': 'SERVICE USER NAME PASSWORD', # Specify organization units where users search will be executed. # Follow pattern (e.g. OU=DEV,DC=domain,DC=com) 'SEARCH_GROUPS': 'OU=DEV,DC=testntl,DC=local', }
Open the
/opt/findface-multi/configs/findface-multi-identity-provider/findface-multi-identity-provider.pyconfiguration file and repeat the previous steps.Rebuild all FindFace Multi containers.
cd /opt/findface-multi sudo docker-compose down sudo docker-compose up -d
Manage FindFace Multi Users via Active Directory
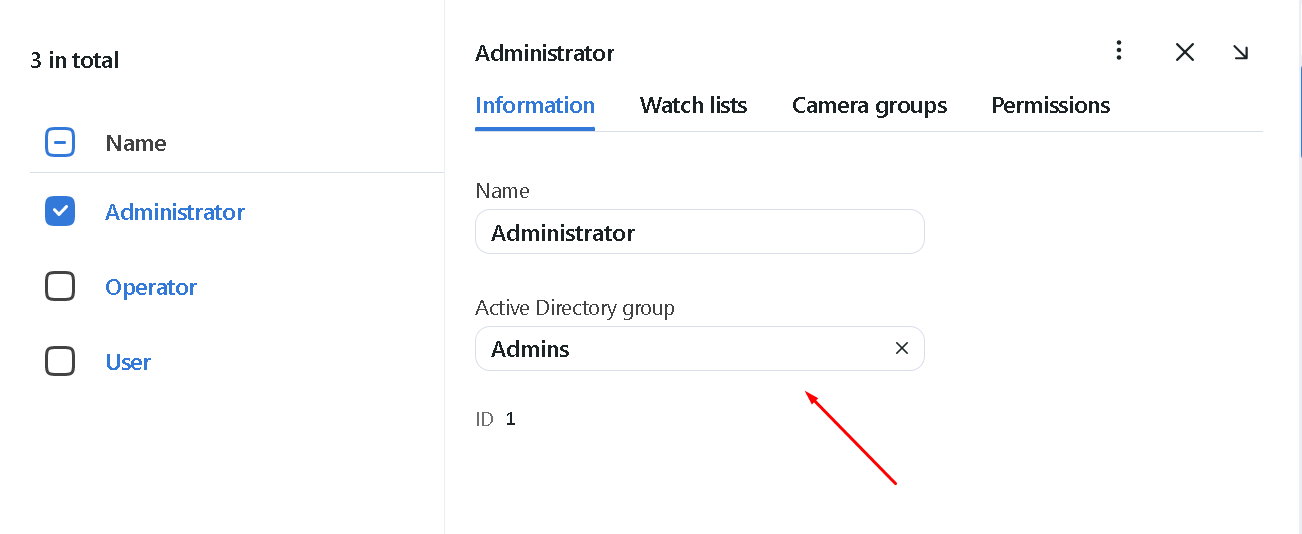
If the FindFace Multi integration with Active Directory is enabled, you will be able to set one of the Active Directory groups for a role you are creating or editing.
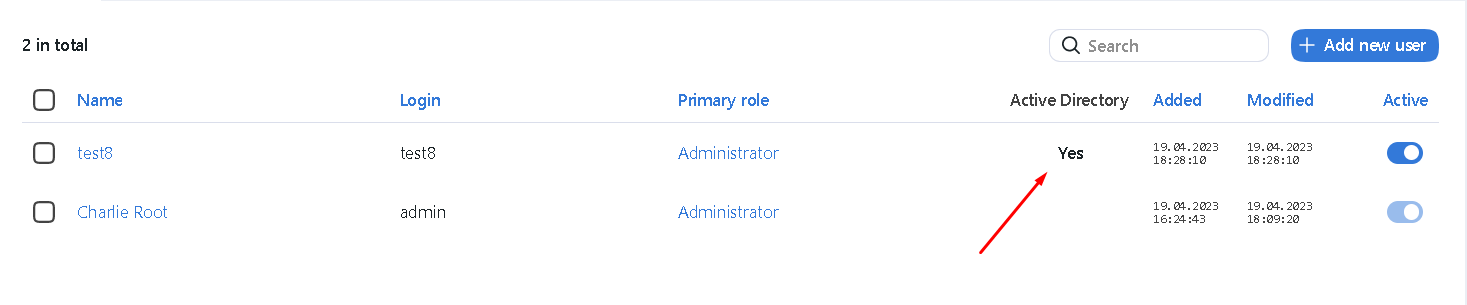
Once a user from the selected Active Directory group logs-in into FindFace Multi for the first time, they will be automatically added to the FindFace Multi user list.
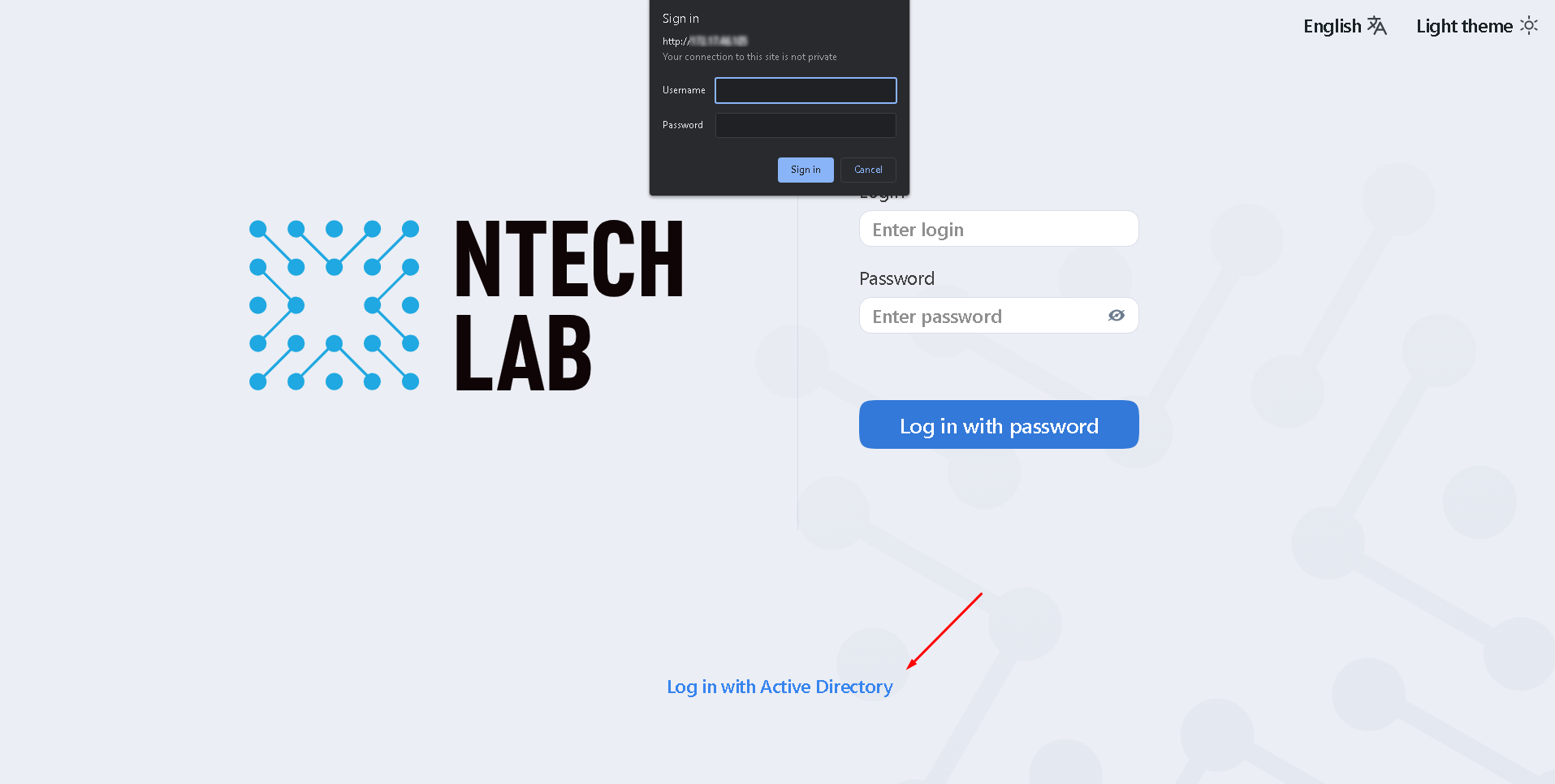
To log-in with Active Directory, a user must click the Log in with Active Directory button in the authentication window, specify their Active Directory credentials, and click Sign in.
Deactivate or Delete Users
In order to deactivate a user, unset Active on the user list ().
If you are going to deactivate multiple users, select them on the user list and then click Deactivate selected.
To delete users from FindFace Multi, select them on the user list and then click Delete selected.